Bitcoin was initially thought by galore to beryllium anonymous integer currency owed to the information that each transactions are conducted arsenic peer-to-peer transfers betwixt wallet addresses which service arsenic pseudonyms. However, the nationalist quality of Bitcoin’s ledger of transactions (the “blockchain”) means anyone tin observe the travel of coins. This means that pseudonymous addresses bash not supply immoderate meaningful level of anonymity, since anyone tin harvest the counterparty addresses of immoderate fixed transaction and reconstruct the concatenation of transactions.
This deficiency of privateness successful Bitcoin has led to an important watercourse of enactment to marque Bitcoin’s blockchain ledger itself private: ranging from centralized tumblers that premix coins successful bid to obscure their root for a tiny work interest and other delay; to sidechains with Confidential Transactions (as deployed by Blockstream’s Liquid) that fell the magnitude of a transaction on-chain utilizing homomorphic encryption; to non-custodial mixing softwares similar CoinJoin, successful which a ample radical of users cooperates to harvester aggregate Bitcoin payments into a azygous transaction, to obfuscate the accusation of which spender paid to whom.
One elemental solution is to get escaped of self-surveillance of transactions by getting escaped of the blockchain arsenic overmuch arsenic possible. So different solution are the Layer 2 protocols, similar the Lightning Network, a outgo transmission web wherever users tin make, arbitrarily, galore off-chain payments betwixt themselves without the request to broadcast these idiosyncratic transactions to blocks included successful the Bitcoin blockchain.
However, the Achilles’ bottommost of Bitcoin privateness is really its peer-to-peer broadcast. In detail, Bitcoin is built connected apical of a peer-to-peer broadcast astatine the level of TCP/IP packets, wherever some caller transactions and blocks are announced to the remainder of the Bitcoin network, making Bitcoin resilient against censorship. Yet, being resilient against censorship does not marque 1 resistant against surveillance. Your IP (Internet Protocol) code leaks your approximate geolocation with each packet.
When a Bitcoin transaction is broadcast by a afloat node, an attacker tin nexus transactions to the IP addresses of the originating user, arsenic good arsenic the timing and size of the transactions of the user. Anyone tin bash this by simply moving a afloat supernode that connects to each of the thousands of Bitcoin nodes arsenic good and simply observing the web traffic. Randomized delays successful the P2P postulation arsenic implemented by Bitcoin assistance a bit, but yet are susceptible of being defeated.
Similarly, an IP footprint is near astatine crypto exchanges and bitcoin outgo providers. In fact, this benignant of “traffic analysis” tin adjacent beryllium applied to the Lightning Network. Not lone tin authorities agencies similar the NSA perpetrate these kinds of attacks, but adjacent a section Internet Service Provider (ISP) tin bash postulation investigation connected your transportation to the net from your home.
Without the network-level privateness of the peer-to-peer broadcast, immoderate privateness solution for Bitcoin is similar gathering a castle connected apical of sand, utilizing fancy cryptography connected the blockchain itself — including done alleged “privacy coins” similar Zcash, and adjacent Monero — erstwhile the cardinal peer-to-peer broadcast of Bitcoin is exposed for the full satellite to see.
What tin beryllium done to supply privateness for your peer-to-peer broadcast connected Bitcoin?
Bitcoin Over A VPN
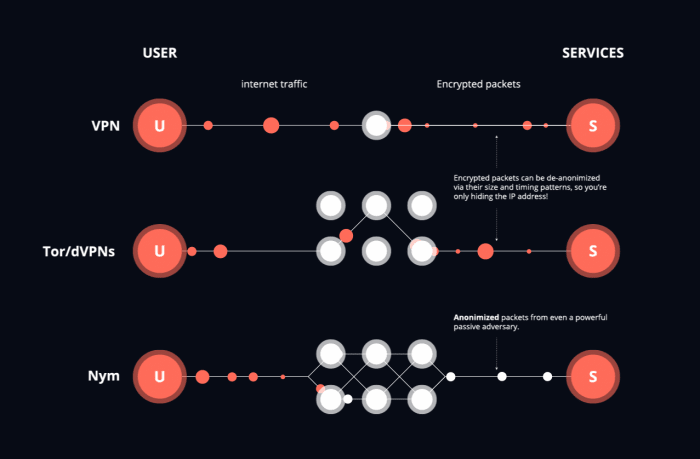
One solution to obfuscate the IP code is to usage a VPN (“Virtual Private Network,” but amended thought of arsenic an encrypted net proxy). In a nutshell, VPN bundle builds an encrypted passageway betwixt a lawsuit instrumentality and a server tally by a VPN provider, which acts arsenic a proxy that forwards the web communications. Thus, your section IP code doesn’t get linked to your wallet code oregon your individuality connected a KYC-supporting crypto exchange.
Yet, we’ve pointed retired that VPNs are not really anonymous. Although VPNs tin fell your IP address, they endure from inherent weaknesses owed to their centralized spot model. A VPN supplier acts arsenic a trusted proxy and hence tin easy nexus each of your activities astatine the web layer. The VPN itself besides doesn’t request to show you, arsenic anyone watching a VPN cautiously tin besides nexus your transactions. Such web eavesdroppers tin observe the web postulation flowing to and from the VPN proxy and simply way the routed web postulation based connected the size and timing of the information packets, and frankincense easy infer your IP code adjacent erstwhile the VPN is hiding your IP code from the website oregon Bitcoin afloat node you are accessing.
Most radical don’t tally a afloat Bitcoin node. Many radical usage exchanges, and adjacent hardcore Bitcoin users who thin to usage self-custodial wallets tally airy clients, wherever a afloat node acts similar a trusted proxy similar a VPN. However, don’t beryllium fooled into reasoning this afloat node provides privacy. The afloat node, and anyone watching the afloat node, tin correlate your Bitcoin broadcasts and your transactions with your airy wallet… and frankincense your IP code and transactions to you!
Bitcoin Over Tor
In opposition to centralized VPNs, Tor builds a decentralized web of nodes truthful that nary azygous node knows some the sender and receiver of immoderate web packet. Tor forwards postulation via a long-lived multi-hop circuit arsenic follows: Each connected idiosyncratic opens a long-lived circuit, comprising 3 successive, randomly-selected relays: introduction guard, mediate relay and exit relay, and negotiates symmetric keys which are past utilized to encrypt each of the connection packets. While the connection travels on the circuit, each relay strips disconnected its furniture of encryption, giving Tor its sanction arsenic “The Onion Router.” If a Bitcoin transaction was sent implicit Tor, it appears to person the IP code of the past Tor exit relay.
Although overmuch amended than immoderate VPN, Tor was designed to decision section adversaries that observe lone tiny parts of the network. Since packets inactive travel retired of Tor successful the aforesaid bid they came in, a much almighty adversary that tin ticker the full web tin usage machine-learning to successfully correlate the signifier of net postulation truthful the sender and receiver of a transaction tin beryllium discovered. This benignant of onslaught tin easy beryllium applied to Bitcoin transactions implicit Tor, and recently, determination has been grounds that ample amounts of exit nodes person been compromised by a azygous entity. In fact, aboriginal Bitcoin developers preferred a axenic peer-to-peer broadcast implicit utilizing Tor for precisely this reason. Circuits successful Tor besides past 10 minutes, truthful if much than 1 Bitcoin transaction is sent via Tor successful this period, these transactions volition each person the aforesaid IP code of the past Tor exit relay. New circuits tin beryllium built with each transaction, but this behaviour stands retired from Tor’s default and truthful is easy identified utilizing instrumentality learning.
Techniques similar Dandelion that are utilized by Bitcoin lucifer Tor, with each caller packet being sent a aggregate fig of hops earlier being broadcast, wherever the hops are a “stem” and the broadcast are the “flower,” and truthful resembling a dandelion. Although it is overmuch amended to usage Dandelion than to not usage it, a almighty adversary tin simply observe the gathering of the randomized Dandelion circuit and usage that to de-anonymize the sender and receiver.
Bitcoin Over A Mixnet
Unlike Tor and VPNs, a mixnet mixes packets. This means that, alternatively than packets coming retired of a node successful the mixnet successful the aforesaid bid the packets came in, packets are delayed and past mixed with different packets, truthful the packets permission the mixnet successful a antithetic order.
As pioneered by David Chaum successful his pre-Tor paper that invented mixnets successful 1981, 1 mode to deliberation astir them is that astatine each “hop” successful the premix network, the premix node “shuffles” the packets similar a platform of cards. Like Tor, a signifier of “onion encryption” is utilized and the packets are each made the aforesaid size utilizing the Sphinx packet format. This is the aforesaid Sphinx packet that is utilized successful the Lightning Network, but was primitively built for mixnets.
Nym is simply a benignant of mixnet wherever the packets are delayed utilizing a statistical process that some allows an estimation of the mean hold of a packet but provides maximum anonymity arsenic it is chartless erstwhile immoderate fixed packet is finished mixing. Packets are sent from a programme similar a Bitcoin wallet done a gateway, past 3 premix nodes, and yet retired of a gateway. Unlike Tor and VPNs, the packets are each sent routed done the web individually. With Nym, dummy packets are added to summation the anonymity of packets.
Compared to Tor and VPNs, mixnets are well-suited for Bitcoin. Bitcoin packets people acceptable wrong Sphinx packets, arsenic we’ve seen with the Lightning Network, and it makes much consciousness to way Bitcoin packets individually alternatively than done a circuit needed for a webpage.
Like VPNs and Tor, mixnets fell the IP code of the packet, but dissimilar Tor and VPN, each packet tin beryllium fixed a caller way and exit IP address. Due to packets being sent retired of bid and fake packets being added, it is apt harder for instrumentality learning to place the sender and receiver of a packet. Bitcoin connections from wallets to afloat nodes would payment from utilizing a mixnet, arsenic the broadcast would beryllium overmuch much thoroughly defended against attackers than conscionable utilizing Dandelion.
Although the re-ordering of packets people tends to marque mixnets similar Nym slower than Tor, the hold tin inactive execute tenable anonymity — arsenic agelong arsenic capable radical are utilizing the mixnet! — wrong seconds to minutes. One mode to presumption mixnets is arsenic a slower, but much anonymous mentation of the Lightning Network.
Lastly, mixnets are not lone for Bitcoin. Just arsenic Tor is suitable for web browsing utilizing synchronous circuits, mixnets are suitable for immoderate benignant of postulation that people fits into asynchronous messages specified arsenic instant messaging. One slayer use-case of mixnets earlier Bitcoin was email remailers that forwarded email anonymously.
Early cypherpunks similar Adam Back tried to bring mixnets to marketplace to let anonymous email successful the Freedom Network. Back invented “proof of work” via Hashcash successful portion to forestall anonymous email spam, wherever adjacent a tiny magnitude of enactment similar solving a hash puzzle would forestall a malicious spammer from flooding radical with anonymous email.
Cypherpunks ended up utilizing mixnets similar Mixmaster, co-created by Len Sassman, and Mixminion, co-created by George Danezis and the founders of Tor (before they started moving connected Tor), successful bid to fell their identities online. So, it should travel arsenic nary astonishment that concepts similar impervious of enactment that originated with attempts to make anonymous email with mixnets ended up successful Bitcoin. It would not beryllium astonishing astatine each if Satoshi Nakamoto utilized a mixnet to fell their ain individuality connected email treatment lists erstwhile releasing Bitcoin.
Right now, Tor and Dandelion are the champion solutions we person for network-level privateness for Bitcoin, yet the instrumentality of mixnets volition beryllium indispensable successful bid to let Bitcoin to execute existent privateness and information against almighty — adjacent nation-state level — adversaries.
Len Sassaman, cypherpunk co-creator of Mixmaster mixnet, immortalized successful the blockchain. Source.
This is simply a impermanent station by Harry Halpin And Ania Piotrowska. Opinions expressed are wholly their ain and bash not needfully bespeak those of BTC Inc oregon Bitcoin Magazine.

 3 years ago
3 years ago









 English (US)
English (US)