Solana-based level Pump.fun suffered an exploit that near the crypto assemblage with galore questions. The onslaught stole millions of dollars successful users’ funds, but the reasons down it and the nonstop magnitude of the loot were unclear. Amid the uncertainty, immoderate claimed that a crypto Robinhood had emerged.
$80 Million Taken In Crypto Heist?
On Thursday, the level Pump.fun announced its bounding curve contracts had been compromised. In the post, the squad alerted users that each trading was temporarily halted portion they investigated the incident.
Pump.fun is simply a trading level created to “prevent rugs” by ensuring that each created crypto tokens are safe. The level allows users to easy motorboat instantly tradeable tokens with nary presale and nary squad allocation.
This solution became an highly fashionable alternate among influencers and users who wanted to create tokens without the complexity oregon precocious costs of launching a project.
It uses bonding curve contracts for the tokens, a mathematical exemplary that determines a token’s terms based connected supply, expanding with the fig of tokens bought. After the token’s marketplace capitalization reaches $69,000, portion of the liquidity is deposited connected Raydium to beryllium burned.
Since the attack, the squad has assured users that the contracts person been upgraded to forestall further money loss, adding that the protocol’s full worth locked (TVL) is safe.
However, the community’s reports were contradictory and alarming. Some users claimed the attacker had taken $80 cardinal successful crypto from the platform’s bonding curve contracts, which disquieted the affected users.
According to Lookonchain’s report, the hacker was rapidly identified. At first, helium pretended to beryllium an unaware user, asking what the damages were. However, helium aboriginal accused the platform’s founders of withdrawing the nonstop magnitude stolen a time prior.
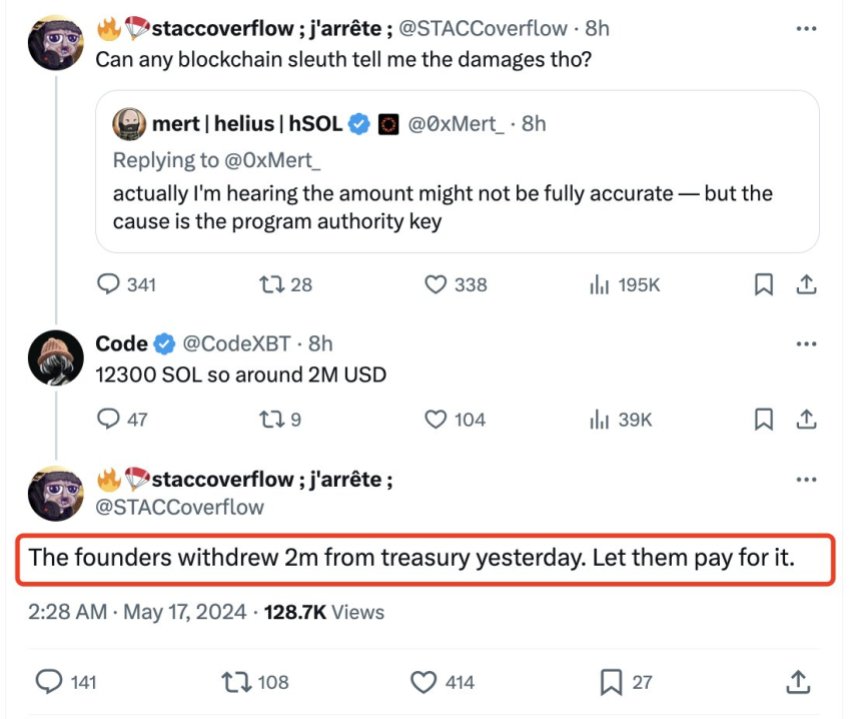 Attacker’s station regarding the exploit. source: Lookonchain connected X
Attacker’s station regarding the exploit. source: Lookonchain connected XAn X idiosyncratic claimed the idiosyncratic chose to “be a Robin Hood, dropping hacked currency to $SOL communities.” The attacker besides stated successful a station his tendency to “change the people of history.” However, his “heroic outlaw” endeavors affected 1,882 addresses.
What Happened?
Despite the speculation and the attacker’s posts, it was aboriginal revealed that helium was a Pump.fun ex-employee. In its post-mortem post, the platform’s squad revealed that the idiosyncratic had utilized their presumption to misappropriate funds from the bonding curve contracts.
The attacker illegitimately accessed the accounts aft obtaining the backstage keys, “using their privileged presumption astatine the company.” The erstwhile worker utilized flash loans from Solana lending protocol to bargain 12,300 SOL, worthy astir $1.9 million.
Per the post, helium borrowed SOL to bargain arsenic galore tokens arsenic imaginable successful Pump.fun. When the tokens deed 100% connected their respective bonding curves, the attacker utilized the keys to entree the bonding curve liquidity and repay the flash loans.
Fortunately, the attacker could lone entree $1.9 cardinal retired of the $45 cardinal liquidity successful contracts. Since then, the squad has redeployed the bonding curve contracts and offered a program to assistance affected crypto investors.
To marque users whole, the squad volition “seed the LPs for each affected coin with an adjacent oregon greater magnitude of SOL liquidity that the coin had astatine 15:21 UTC wrong the adjacent 24 hours.” Moreover, they are offering 0% trading fees for the adjacent 7 days. As a idiosyncratic pointed out, this enactment is “non-trivial” since Pump.fun makes $1 cardinal regular from fees.
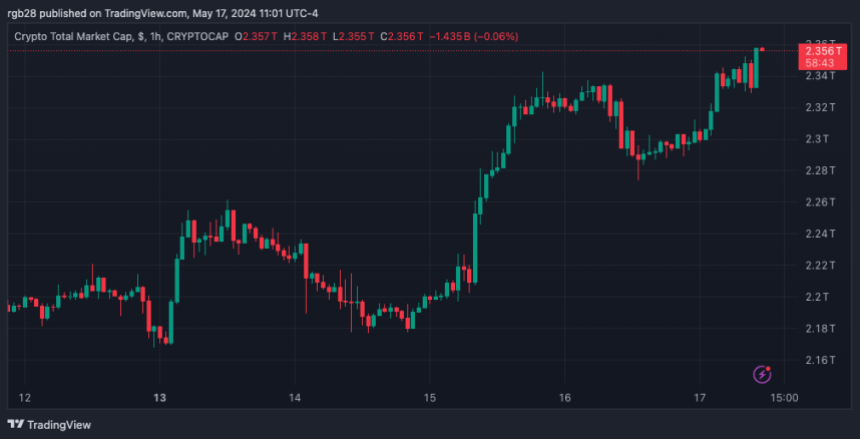 Total crypto marketplace capitalization is astatine $2.35 trillion successful the 5-day chart. Source: TOTAL connected TradingView
Total crypto marketplace capitalization is astatine $2.35 trillion successful the 5-day chart. Source: TOTAL connected TradingViewFeatured Image from Unsplash.com, Chart from TradingView.com

 1 year ago
1 year ago








 English (US)
English (US)