On January 23, Wallet Connect and different web3 companies informed their users astir a phishing scam utilizing authoritative web3 companies’ email addresses to bargain funds from thousands of crypto wallets.
A Massive Phishing Campaign
Wallet Connect took X to notify its assemblage astir an authorized email sent from a Wallet Connect-linked email address. This email prompted the receivers to unfastened a nexus to assertion an airdrop, however, the nexus led to a malicious tract and, arsenic Wallet Connect confirmed, it was not issued straight by the squad oregon anyone affiliated. Wallet Connect contacted web3 information and privateness steadfast Blockaid to analyse the phishing scam further.
We've detected a blase phishing onslaught impersonating @WalletConnect via a fake email linking to a malicious dapp.
Blockaid enabled wallets are safe.https://t.co/quz9olGrpZ pic.twitter.com/TYS0BjIk2J
— Blockaid (@blockaid_) January 23, 2024
In the pursuing hours, crypto sleuth posted a assemblage alert to pass unaware users that CoinTelegraph, Token Terminal, and De.Fi squad emails were besides compromised, signaling that a monolithic and much blase phishing run was happening. At the clip of the post, astir $580K had been stolen.
After investigating, Blockaid aboriginal revealed that the attacker “was capable to leverage a vulnerability successful email work supplier MailerLite to impersonate web3 companies.”
Email phishing scams are communal among cyber scammers, making users wary of astir suspicious links oregon emails. At the aforesaid time, companies and entities counsel against opening links that bash not travel from their authoritative channels. In this case, the attacker was capable to instrumentality a immense fig of users from these companies arsenic the malicious links came from their authoritative email addresses.
The compromise allowed the attacker to nonstop convincing emails with malicious links attached that led to wallet drainer websites. Specifically, the links led to respective malicious dApps that utilize the Angel Drainer Group infrastructure.
The attackers, arsenic Bloackaid explained, took vantage of the information antecedently provided to Mailer Lite, arsenic it had been fixed entree by these companies to nonstop emails connected behalf of these sites’ domains before, specifically utilizing pre-existing DNS records, arsenic elaborate successful the thread:
Specifically, they utilized “dangling dns” records which were created and associated with Mailer Lite (previously utilized by these companies). After closing their accounts these DNS records stay active, giving attackers the accidental to assertion and impersonate these accounts. pic.twitter.com/cbTpc5MXu1
— Blockaid (@blockaid_) January 23, 2024
MailerLite Explains Security Breach
The mentation aboriginal came Via an email, wherever MailerLite explained that the probe showed that a subordinate of their lawsuit enactment squad inadvertently became the initial constituent of the compromise. As the email explains:
The squad member, responding to a lawsuit enquiry via our enactment portal, clicked connected an representation that was deceptively linked to a fraudulent Google sign-in page. Mistakenly entering their credentials there, the perpetrator(s) gained entree to their account. The intrusion was inadvertently authenticated by the squad subordinate done a mobile telephone confirmation, believing it to beryllium a morganatic entree attempt. This breach enabled the perpetrators) to penetrate our interior admin panel.
MailerLite further adds that the attacker reset the password for a circumstantial idiosyncratic connected the admin sheet to consolidate the unauthorized power further. This power gave them entree to 117 accounts, of which they lone focused connected cryptocurrency-related accounts for the phishing run attack.
An anonymous Reddit idiosyncratic posted an investigation of the concern and gave a person look astatine the attacker’s transactions. The idiosyncratic revealed:
One unfortunate wallet appears to person mislaid 2.64M worthy of XB Tokens. I’m showing astir 2.7M sitting successful the phishing wallet of 0xe7D13137923142A0424771E1778865b88752B3c7, portion 518.75K went to 0xef3d9A1a4Bf6E042F5aaebe620B5cF327ea05d4D.
The idiosyncratic stated that astir stolen funds were successful the archetypal phishing address. At the aforesaid time, astir $520,000 worthy of ETH were sent to privateness protocol Railgun, and helium believes that they volition soon beryllium moved done different mixer oregon exchange.
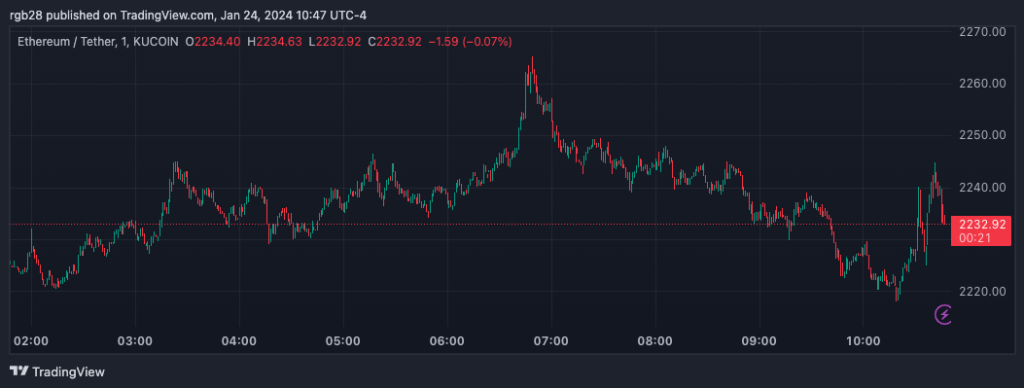
Featured representation from Unsplash.com, Chart from TradingView.com
Disclaimer: The nonfiction is provided for acquisition purposes only. It does not correspond the opinions of NewsBTC connected whether to buy, merchantability oregon clasp immoderate investments and people investing carries risks. You are advised to behaviour your ain probe earlier making immoderate concern decisions. Use accusation provided connected this website wholly astatine your ain risk.

 2 years ago
2 years ago






 English (US)
English (US)