The U.S. Department of Justice (DOJ) announced successful a February 2022 statement that it had successfully seized the bulk of the bitcoin drained successful a 2016 hack of the cryptocurrency speech Bitifinex aft gaining power of the wallet supposedly containing the stolen funds.
Despite the evident unlikelihood of retaking long-gone funds, a analyzable but deterministic way of grounds allowed instrumentality enforcement to drawback Ilya Lichtenstein and Heather Morgan, a mates that was allegedly trying to obfuscate the amerciable origins of the bitcoin they had been leveraging to flex shiny lifestyles done a analyzable wealth laundering scheme.
But what seemed to beryllium a carefully-thought-out scam really turned retired to beryllium a rather fragile 1 filled with missteps, which facilitated the enactment of peculiar cause Christopher Janczewski, assigned to the Internal Revenue Service’s transgression probe portion (IRS-CI). This enactment yet led to Janczewski filing a complaint with justice Robin Meriweather to complaint Lichtenstein and Morgan for wealth laundering conspiracy and conspiracy to defraud the United States.
This nonfiction takes a heavy dive into the nuances of the instrumentality enforcement enactment that uncovered the identities of the accused Bitfinex hackers, and into the steps of the charged couple, relying connected the accounts provided by the DOJ and peculiar cause Janczewski. However, since important aspects of the probe person not been disclosed by authoritative documents, the writer volition supply plausible scenarios and imaginable explanations to questions that stay unanswered.
How Did Law Enforcement Seize The Stolen Bitfinex Bitcoin?
Bitcoin proponents often boast astir the monetary system’s set of principles that enables a precocious grade of sovereignty and absorption to censorship, making Bitcoin transactions intolerable to beryllium stopped and bitcoin holdings intolerable to beryllium seized. But, if that is true, however past was instrumentality enforcement capable to instrumentality a clasp of the launderers’ bitcoin successful this case?
According to the ailment filed by peculiar cause Janczewski, instrumentality enforcement was capable to get wrong Litchestein’s unreality retention wherever helium kept overmuch if not each of the delicate accusation related to his operations arsenic helium attempted to cleanable the soiled funds — including the backstage keys of the Bitcoin wallet holding the largest information of stolen BTC.
The censorship absorption of Bitcoin transactions and the sovereignty of bitcoin funds beryllium connected the due handling of the associated private keys, arsenic they are the lone mode to determination bitcoin from 1 wallet to another.
Even though Lichtenstein’s backstage keys were kept successful unreality storage, according to the DOJ they were encrypted with a password truthful agelong that adjacent blase attackers would astir apt not person been capable to ace it successful their lifetime. The DOJ did not respond to a petition for remark connected however it was capable to decrypt the record and entree the backstage keys.
There are a fewer plausible scenarios for however instrumentality enforcement was capable to ace Lichtenstein’s encryption. Though not insecure successful and of itself, symmetric encryption, which leverages an encryption password for some encrypt and decrypt functions, is lone arsenic unafraid arsenic its password and that password’s storage.
Therefore, the archetypal anticipation relates to the information of the password’s storage; instrumentality enforcement could person obtained entree to the password someway and didn’t request to brute unit its mode done the files successful the cloud. An alternate method for instrumentality enforcement being capable to decrypt Lichtenstein’s files could impact it having truthful overmuch much idiosyncratic accusation astir the mates and computing powerfulness than immoderate different blase attacker successful the satellite that a tailored onslaught to decrypt targeted files could really beryllium viable portion not contradicting the DOJ’s statements. We besides don’t cognize the algorithm utilized successful the encryption strategy — immoderate are much robust than others and variations successful the aforesaid algorithm besides airs antithetic information risks — truthful the circumstantial algorithm utilized mightiness person been much susceptible to cracking, though this would contradict the DOJ claims regarding crackability above.
The astir apt lawsuit of the 3 is arguably that instrumentality enforcement didn’t request to decrypt the record successful the archetypal place, which makes sense, particularly fixed the DOJ comments above. Special cause Janczewski and his squad could person gained entree to the password someway and wouldn’t request to brute unit its mode done the unreality storage’s files. This could beryllium facilitated by a 3rd enactment that Lichtenstein entrusted with the instauration oregon retention of the decryption password, oregon done immoderate benignant of misstep by the mates that led to the password being compromised.
Why Keep Private Keys On Cloud Storage?
The crushed wherefore Lichtenstein would support specified a delicate record successful an online database is unclear. However, immoderate speculation relates to the underlying hack — an enactment for which the mates has not been charged by instrumentality enforcement — and the request for having the wallet’s backstage keys kept connected the unreality “as this allows distant entree to a 3rd party,” according to a Twitter thread by Ergo from OXT Research.
The practice presumption besides supports the lawsuit for symmetric encryption. While asymmetric encryption is good designed for sending and receiving delicate information — arsenic the information is encrypted utilizing the recipient’s nationalist cardinal and tin lone beryllium decrypted utilizing the recipient’s backstage cardinal — symmetric encryption is cleanable for sharing entree to a stationary record arsenic the decryption password tin beryllium shared betwixt the 2 parties.
An alternate crushed for keeping the backstage keys online would beryllium elemental deficiency of care. The hacker could simply person thought their password was unafraid capable and fell for the convenience of having it connected a unreality work that tin beryllium accessed anyplace with an net connection. But this script inactive doesn’t reply the question of however the mates got entree to the backstage keys related to the hack.
Keeping the backstage cardinal online for convenience makes sense, provided the hackers lacked capable method cognition to guarantee a beardown capable symmetric encryption setup oregon simply assumed their statement couldn’t beryllium breached.
Bitfinex declined to remark connected immoderate details known astir the hacker oregon whether they are inactive being tracked down.
“We cannot remark connected the specifics of immoderate lawsuit nether investigation,” Bitfinex CTO Paolo Ardoino told Bitcoin Magazine, adding that determination are “inevitably a assortment of parties involved” successful “such a large information breach.”
How Did Lichtenstein And Morgan Get Caught?
The ailment and DOJ’s connection alleges that the mates employed respective techniques to effort to launder the bitcoin, including concatenation hopping and the usage of pseudonymous and concern accounts astatine respective cryptocurrency exchanges. So, however did their movements get spotted? It mostly boils down to patterns and similarities paired with carelessness. Bitfinex besides “worked with planetary instrumentality enforcement agencies and blockchain analytics firms” to assistance retrieve the stolen bitcoin, Ardoino said.
Lichtenstein would often unfastened up accounts connected bitcoin exchanges with fictitious identities. In 1 circumstantial case, helium allegedly opened 8 accounts connected a azygous speech (Poloniex, according to Ergo), which astatine archetypal were seemingly unrelated and not trivially linkable. However, each of those accounts shared aggregate characteristics that, according to the complaint, gave the couple’s individuality away.
First, each of the Poloniex accounts utilized the aforesaid email supplier based successful India and had “similarly styled” email addresses. Second, they were accessed by the aforesaid IP code — a large reddish emblem that makes it trivial to presume the accounts were controlled by the aforesaid entity. Third, the accounts were created astir the aforesaid time, adjacent to the Bitfinex hack. Additionally, each accounts were abandoned pursuing the exchange’s requests for further idiosyncratic information.
The ailment besides alleges that Lichtenstein joined aggregate bitcoin withdrawals unneurotic from antithetic Poloniex accounts into a azygous Bitcoin wallet cluster, aft which helium deposited into an relationship astatine a bitcoin speech (Coinbase, according to Ergo), for which helium had antecedently provided know-your-customer (KYC) information.
“The relationship was verified with photographs of Lichtenstein’s California driver’s licence and a selfie-style photograph,” per the complaint. “The relationship was registered to an email code containing Lichtenstein’s archetypal name.”
By assuming that helium had already cleansed the bitcoin, and sending it to a KYC’d account, Lichtenstein undid the pseudonymity the erstwhile accounts had accomplished with India-based email accounts, arsenic helium hinted to instrumentality enforcement that helium owned the funds from those archetypal withdrawals that were clustered together. And the ailment alleges that Lichtenstein besides kept a spreadsheet successful his unreality retention containing elaborate accusation astir each 8 Poloniex accounts.
When it comes to on-chain data, Ergo told Bitcoin Magazine that it is intolerable for a passive perceiver to measure the validity of galore of the complaint’s claims since the darknet marketplace AlphaBay was utilized aboriginal connected arsenic a passthrough.
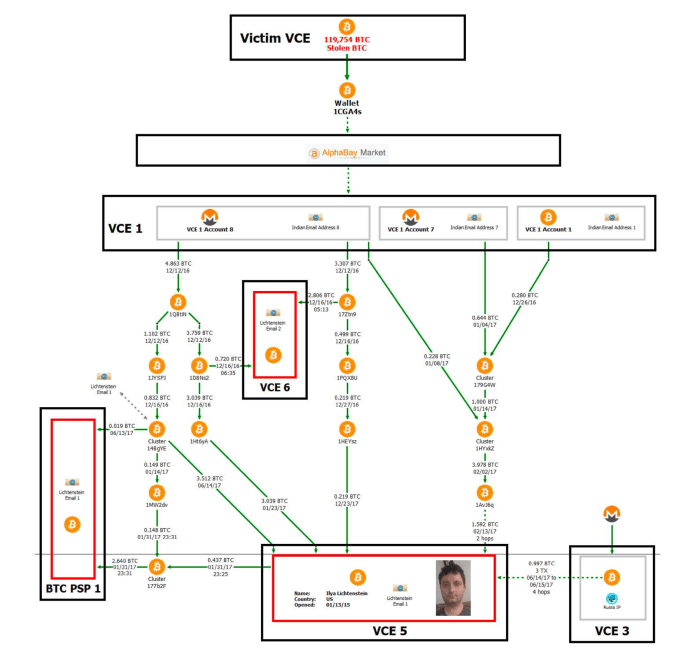
The ailment details the travel of funds aft the Bitfinex hack, but the AlphaBay transaction accusation isn’t auditable by outsider observers, who truthful cannot hint the funds themselves. Image source: DOJ.
“The probe is precise straight-forward, but it requires insider cognition of cross-custodial entity flows,” Ergo told Bitcoin Magazine. “For example, the [U.S. government] and concatenation surveillance firms person shared the AlphaBay transaction past which has nary existent on-chain fingerprint and we don’t person entree to that information. That’s astir wherever I person to halt immoderate investigation arsenic a passive observer.”
Another cardinal portion of accusation is wallet clump “36B6mu,” which was formed by bitcoin withdrawals from 2 accounts astatine Bittrex, according to Ergo, which had been wholly funded by Monero deposits. Wallet clump 36B6mu was past utilized to money antithetic accounts astatine different bitcoin exchanges, which, though it did not incorporate KYC accusation connected the couple, according to the complaint, 5 antithetic accounts astatine the aforesaid speech utilized the aforesaid IP address, hosted by a unreality supplier successful New York. As the supplier handed its records to instrumentality enforcement, it was identified that that IP was leased by an relationship successful the sanction of Lichtenstein and tied to his idiosyncratic email address.
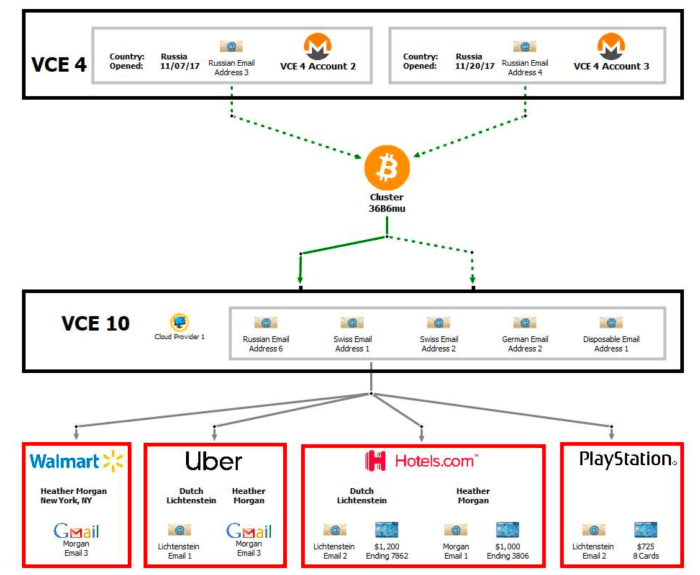
The mates assumed that by backing an speech relationship with Monero and withdrawing BTC they would person “clean” funds, however, a consequent way of KYC accusation was utilized to deanonymize their fictitious identities crossed antithetic custodial services. Image source: DOJ.
Ergo said the OXT squad wasn’t capable to validate immoderate claims astir the 36B6mu cluster.
“We searched for the 36B6mu code that would correspond to the clump and recovered a azygous address,” Ergo said, sharing a link to the code found. “But the code is not portion of a accepted wallet cluster. Further, the timing and volumes don’t look to correspond with those noted successful the complaint.”
“Maybe it’s a typo? So we weren’t capable to truly validate thing to bash with the 36B6mu cluster,” Ergo added.
Bitcoin Privacy Requires Intention — And Attention
Aside from the sections that cannot beryllium independently attested by outer observers, aft analyzing the complaint, it becomes wide that Lichtenstein and Morgan deposited antithetic levels of spot successful their setup and successful respective services arsenic they allegedly attempted to usage the bitcoin from the hack.
First and foremost, Lichtenstein and Morgan maintained delicate documents online, successful a unreality retention work susceptible to seizure and subpoenas. This signifier increases the chances that the setup could beryllium compromised, arsenic it makes specified files remotely accessible and deposits spot successful a centralized institution — which is ne'er a bully idea. For hardened security, important files and passwords should beryllium kept offline successful a unafraid location, and preferably dispersed retired successful antithetic jurisdictions.
Trust compromised astir of the couple’s efforts successful moving the bitcoin funds. The archetypal work they trusted was the immense darknet marketplace AlphaBay. Though it is unclear however instrumentality enforcement was capable to spot their AlphaBay enactment — adjacent though the darknet marketplace has suffered more than 1 information breach since 2016—– the mates nevertheless seems to person assumed this could ne'er happen. But possibly astir importantly, darknet markets often rise suspicion and are ever a superior absorption of instrumentality enforcement work.
Assumptions are unsafe due to the fact that they tin pb you to driblet down your guard, which often triggers missteps which a savvy perceiver oregon attacker tin leverage. In this case, Lichtenstein and Morgan assumed astatine 1 constituent that they had employed truthful galore techniques to obfuscate the root of funds that they felt harmless successful depositing that bitcoin into accounts possessing their personally-identifiable accusation — an enactment that tin ensue a cascading, backwards effect to deanonymize astir if not each of the erstwhile transactions.
Another reddish emblem successful the couple’s handling of bitcoin relates to clustering unneurotic funds from antithetic sources, which enables concatenation investigation companies and instrumentality enforcement to plausibly presume the aforesaid idiosyncratic controlled those funds — different backwards deanonymization opportunity. There is besides nary grounds of utilizing mixing services by the couple, which can’t erase past activity, but tin supply bully forward-looking privateness if done correctly. PayJoin is different instrumentality that tin beryllium leveraged to summation privateness erstwhile spending bitcoin, though determination is nary grounds of the mates utilizing it.
Lichtenstein and Morgan did effort to bash concatenation hopping arsenic an alternate for obtaining spending privacy, a method that attempts to interruption on-chain fingerprints and thus, heuristic links. However, they performed it done custodial services — mostly bitcoin exchanges — which undermine the signifier and present an unnecessary trusted 3rd enactment that tin beryllium subpoenaed. Chain hopping is decently conducted done peer-to-peer setups oregon atomic swaps.
Lichtenstein and Morgan besides tried utilizing pseudonymous, oregon fictitious, identities to unfastened accounts astatine bitcoin exchanges to conceal their existent names. However, patterns successful doing truthful led observers to go much alert of specified accounts, portion an IP code successful communal removed doubts and enabled instrumentality enforcement to presume the aforesaid entity controlled each of those accounts.
Good operational information generally requires that each individuality beryllium wholly isolated from others by utilizing its ain email supplier and address, having its ain unsocial sanction and astir importantly, utilizing a abstracted device. Commonly, a robust setup volition besides necessitate each antithetic individuality to usage a antithetic VPN supplier and relationship that does not support logs and does not person immoderate ties to that user’s existent satellite identity.
Since Bitcoin is simply a transparent monetary network, funds tin easy beryllium traced crossed payments. Private usage of Bitcoin, therefore, requires cognition astir the functioning of the web and utmost attraction and effort implicit the years to guarantee the littlest magnitude of missteps arsenic imaginable portion abiding by wide operational guidelines. Bitcoin isn’t anonymous, but it isn’t flawed either; usage of this sovereign wealth requires volition — and attention.
What Will Happen To The Recovered Bitcoin?
Although the mates person been charged with 2 offenses by U.S. instrumentality enforcement, determination volition inactive beryllium a judging process successful tribunal to find whether they are recovered blameworthy oregon not. In the lawsuit that the mates is recovered blameworthy and the funds are sent backmost to Bitfinex, the speech has an enactment plan, Ardoino told Bitcoin Magazine.
“After the 2016 hack, Bitfinex created BFX tokens, and gave them to affected customers astatine the complaint of 1 coin for each $1 lost,” Ardoino said. “Within 8 months of the information breach, Bitfinex redeemed each the BFX tokens with dollars oregon by exchanging the integer tokens, convertible into 1 communal stock of the superior banal of iFinex Inc. Approximately 54.4 cardinal BFX tokens were converted.”
Monthly redemptions of BFX tokens started successful September 2016, Ardoino said, with the past BFX token being redeemed successful aboriginal April of the pursuing year. The token had begun trading astatine astir $0.20 but gradually accrued successful worth to astir $1.
“Bitfinex besides created a tradeable RRT token for definite BFX holders that converted BFX tokens into shares of iFinex,” Ardoino explained. “When we successfully retrieve the funds we volition marque a organisation to RRT holders of up to 1 dollar per RRT. There are astir 30 cardinal RRTs outstanding.”
RRT holders person a precedence assertion connected immoderate recovered spot from the 2016 hack, according to Ardoino, and the speech whitethorn redeem RRTs successful integer tokens, currency oregon different property.

 3 years ago
3 years ago








 English (US)
English (US)