By combining chat logs leaked successful February with consequent investigation of blockchain data, researchers person gleaned caller insights astir the infamous Conti ransomware gang.
The pack utilized over-the-counter (OTC) brokers successful Russia to currency retired crypto extorted from victims and to wage members for their work, according to a CoinDesk reappraisal of the leaked chats.
At slightest 1 U.S. infirmary attacked by the Conti ransomware during the coronavirus pandemic paid the ransom, the hackers’ interior communications show.
Ransom payouts to the pack whitethorn person been arsenic precocious arsenic 725 BTC and more, according to an investigation by Crystal Blockchain released Tuesday.
New wallets Conti utilized person been located, Crystal said.
In February, a hacker leaked a notorious ransomware gang’s chat logs, offering a uncommon peek wrong the mundane operations of this transgression concern and cryptocurrency’s captious relation successful it. But blockchain information helps overgarment a fuller picture.
The leaked messages showed the Conti hackers had much victims than antecedently reported. They besides revealed that immoderate of those organizations paid to get their IT systems back, and that the pack had ties to different infamous cybercriminal ring, known arsenic Ryuk. Perhaps astir importantly, the cache revealed Conti’s antecedently chartless bitcoin (BTC) wallet addresses.
That served arsenic a jumping-off constituent for on-chain sleuths to capable successful much pieces of the puzzle. For example, blockchain information shows astatine slightest 1 of the U.S. hospitals attacked during the pandemic mightiness person paid ransom to the Conti hackers.
CoinDesk reviewed the Conti members’ leaked messages and analyzed the hackers’ crypto wallets and transactions with assistance from the on-chain analytics steadfast Crystal Blockchain. The workout underscored an enduring paradox of crypto: While an ungated web with unblockable transactions is highly utile for criminals, the nationalist ledger leaves a way of crumbs for instrumentality enforcement and researchers to find later.
Ransomware gangs are a menace calved of the cyber age. While the devastation they dispersed successful corporations is sometimes disposable and tangible (remember the state shortage provoked by the Colonial Pipeline attack past year?), their identities and the mode they run stay mostly concealed.
Now, the curtain has parted somewhat arsenic an indirect effect of the warfare successful Ukraine.
On Feb. 25, the Conti radical declared its allegiance to the Russian authorities pursuing the penetration of Ukraine. On its authoritative website, Conti threatened to retaliate against the West successful effect to imaginable cyber attacks against Russia. This cyber saber-rattling appears to person provoked the leaks, which appeared successful respective places.
A Ukrainian information researcher who obtained entree to the group’s IT infrastructure leaked the messages that accumulated connected the gang’s interior Jabber/XMPP server from 2020 to 2021 to journalists and information researchers, according to CNN. Other media reports suggested the leak was made by a disgruntled Ukrainian subordinate of the Conti gang. The archived messaged were published by a Twitter relationship dedicated to researching malware strains, known arsenic @vxunderground.
“Conti ransomware radical antecedently enactment retired a connection siding with the Russian government. Today a Conti subordinate has begun leaking information with the connection ‘F**k the Russian government, Glory to Ukraine!’" tweeted @vxunderground.
The leaked communications of the Conti pack offers immoderate visibility into however antithetic ransomware strains tin beryllium related.
According to Conti’s messages, the radical has been moving with assorted ransomware strains and groups operating those strains: members notation moving with Ryuk, Trikbot and Maze ransomware. According to the messages, Conti members not lone ran their ain ransomware concern but besides provided tools and services for different hacker groups.
For example, connected June 23, 2020, the group’s leader, nicknamed Stern, tells a lower-level manager known arsenic Target, successful Russian: “Ryuk is going to get backmost from abrogation soon. He volition instrumentality each the bots that we have. For him, we request 5k companies.” (It’s not wide from the preceding and pursuing messages which companies Stern meant.)
The messages besides near a fiscal hint of this partnership: a bitcoin transaction betwixt the Conti and Ryuk gangs, mentioned by Crystal Blockchain successful a March blog post.
In September 2019, 1 of the bitcoin wallets associated with Conti sent 26.25 BTC (worth astir $200,000 astatine the time) to a wallet associated with Ryuk, blockchain information shows.
“Payment accusation contained successful the leaked chats powerfully supports this transportation and that Conti apt tried to interaction Ryuk,” Crystal said successful a blog post. “We besides observed that Ryuk sent payments straight to a Conti wallet that was mentioned successful the chat past respective times; this suggests affiliation and immoderate grade of operational coordination betwixt these 2 groups.”
Earlier, cybersecurity researchers pointed astatine a imaginable connection betwixt the operators of Ryuk and Conti ransomware due to the fact that the malware contained akin pieces of code. However, fiscal connections betwixt the Ryuk and Conti attackers hadn’t been revealed before.
Advanced Intel's Vitali Kremez told Bleeping Computer the ransomware strain Conti uses has been changing hands galore times implicit respective years, starting arsenic Hermes successful 2017. Then it was supposedly purchased by different hackers and turned into Ryuk (possibly named aft a Japanese manga character). Then, the radical “splintered, re-branded oregon decided to modulation to the ‘Conti’ name, which appears to beryllium based disconnected the codification from Ryuk mentation 2,” Bleeping Computer wrote.
Conti operated during the coronavirus pandemic and attacked wellness attraction organizations worldwide, much than fractional of which were located successful the U.S., according to the FBI. Cybersecurity experts person agelong suspected Conti’s transportation to the Russian state, on with galore different ransomware gangs.
Ryuk is known for hacking The New York Times and The Wall Street Journal’s publishing facilities successful 2018, arsenic good arsenic respective different companies. Both Ryuk and Conti utilized a variant of AES-256 encryption to encrypt victims’ files and extort ransom for decryption keys.
The leaked messages besides radiance airy connected the breadth of companies successfully attacked, galore of which had not been antecedently reported.
Minnesota-based Ridgeview Medical Center was famously attacked successful 2020, the archetypal twelvemonth of the pandemic, on with a scope of different U.S. wellness attraction organizations, by the Ryuk and Trickbot malware strains. The Conti radical was, apparently, down those attacks, too: The members speech astir successfully hacking into Ridgeview’s web and encrypting the information the aesculapian halfway needed to operate.
According to Crystal, a transaction connected Oct. 30, 2020, is astir apt the 301 BTC outgo (over $4 cardinal astatine the time) Ridgeview sent to Conti arsenic a ransom.
A time earlier, connected Oct. 29, Conti members Target and Stern mentioned that Ridgeview was acceptable to wage $2 million, oregon 151 BTC; however, Conti’s expected partner, the organizer of the attack, “wanted 300 BTC.”
Later, according to the chat logs, the hackers prevailed, and connected Oct. 30, 301 BTC were sent from an address attributed to the Gemini crypto speech to a wallet that appears to beryllium indirectly related to another wallet, which Conti members mentioned successful the chats arsenic a outgo code for extortion, according to Crystal.
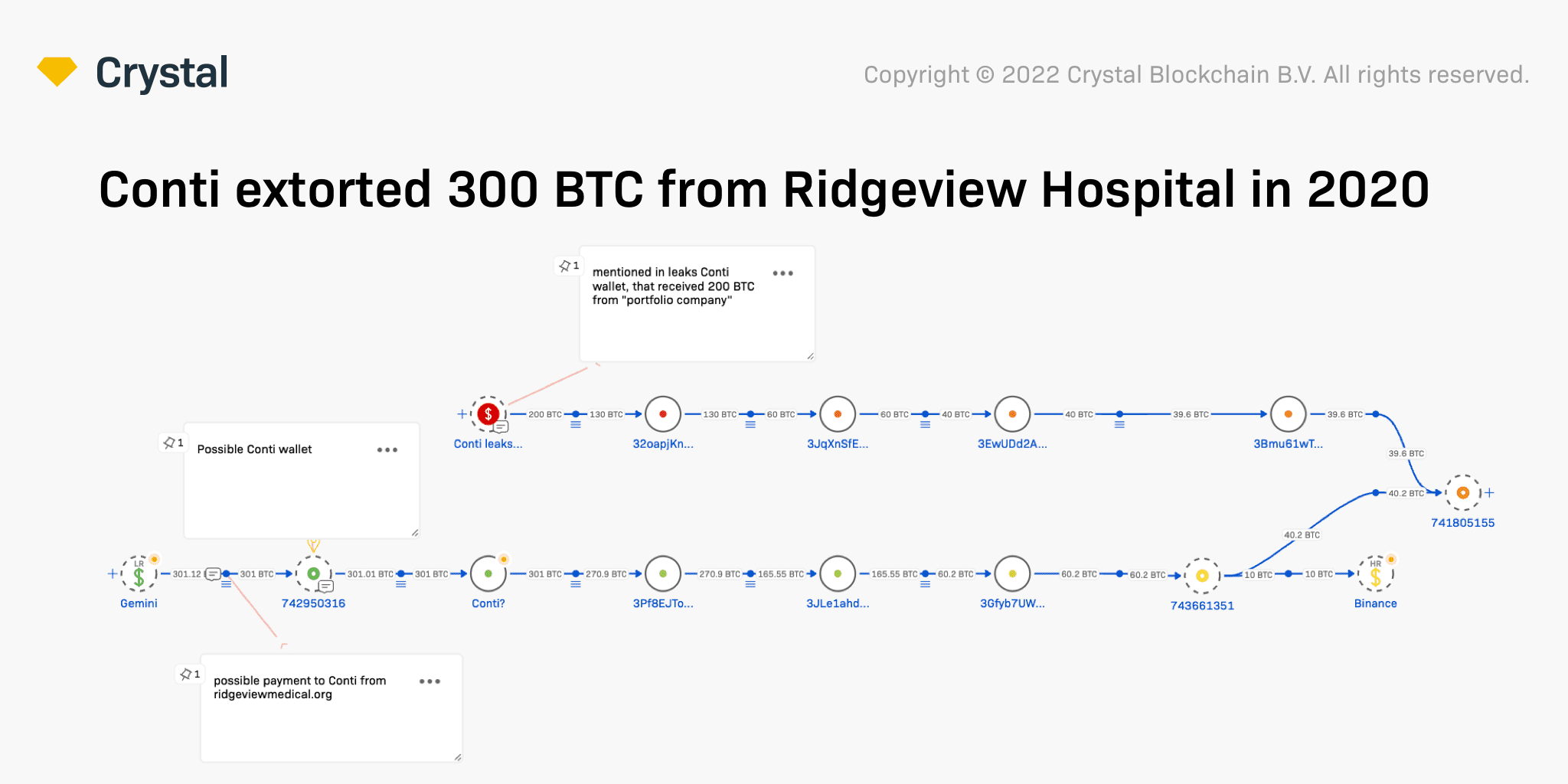
301 BTC outgo to Conti / Crystal Blockchain
Ridgeview did not instrumentality CoinDesk’s petition for remark by property time.
It’s worthy remembering that blockchain investigation to a definite grade is based connected assumptions, and the attribution of a blockchain code to a definite real-life entity astir ne'er is 100% precise. However, Crystal said it is rather assured successful this one: Transfers of hundreds of BTC don’t hap each day.
“The methodology we utilized was to look for related transactions that were astatine the aforesaid worth of the ransom request and discussed successful the group,” said Crystal’s manager of blockchain intelligence, Nick Smart. He added that Crystal had “90% confidence” the transaction was the ransom outgo successful question, fixed its timing, magnitude and transportation to the earlier reported Conti wallets.
There were other, adjacent larger payments the transgression radical managed to gather.
The largest ransom an unidentified unfortunate institution paid to Conti, according to the chat logs, was 725 BTC, Crystal found. That chunk of bitcoin, equivalent to astir $8 cardinal astatine the time, was paid by the Chicago-based employment marketplace CareerBuilder, Crystal said, arsenic the institution was mentioned successful the chats related to the 725 BTC payout.
The receiver of that outgo could person been this bitcoin wallet, Crystal told CoinDesk. On Oct. 10, 2020, the code received 725 BTC and instantly sent it on, to different code not associated with immoderate crypto service, on-chain information shows. There were nary different transactions involving the address, but these two.
CareerBuilder did not respond CoinDesk's petition for comment.
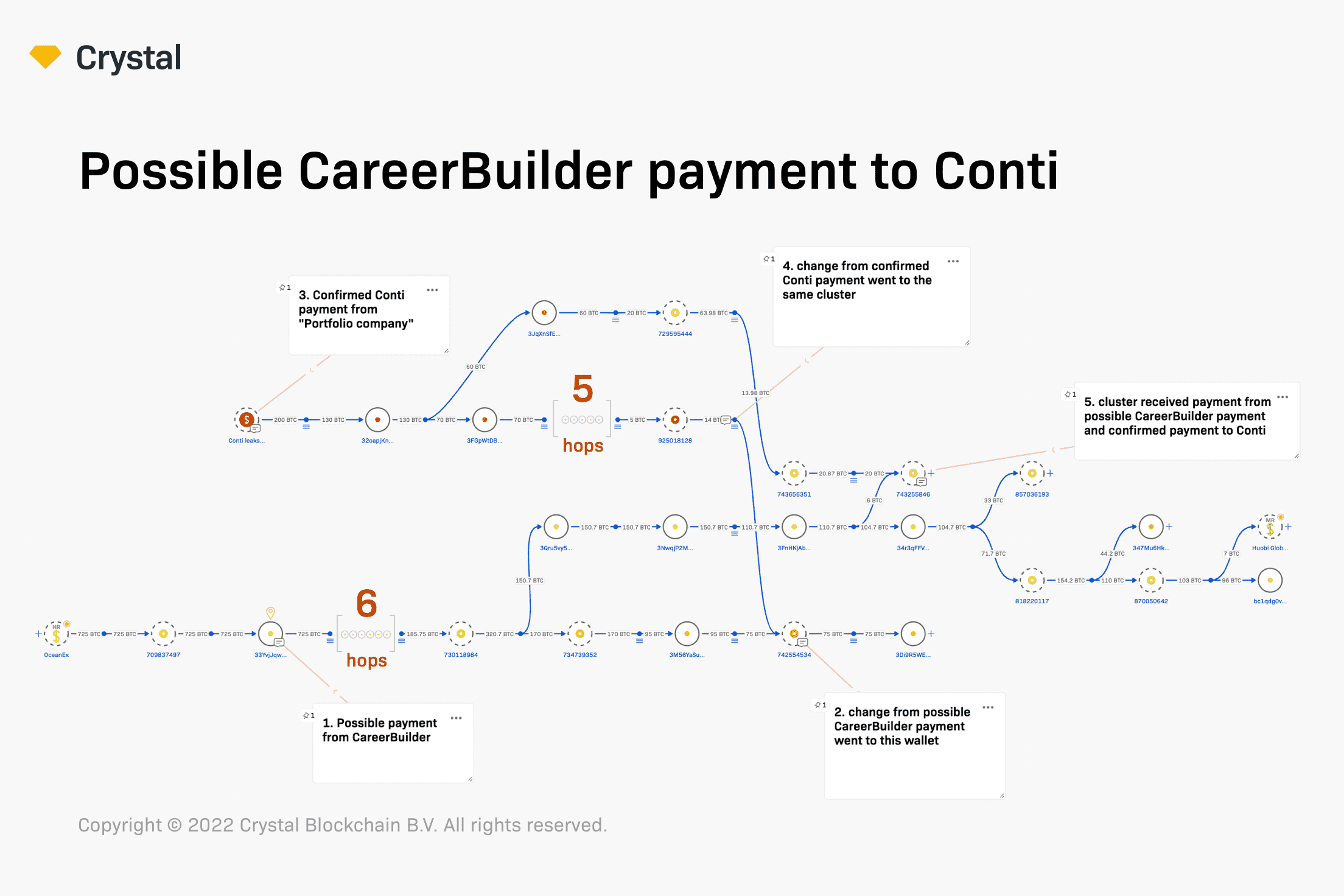
725 BTC outgo to Conti / Crystal Blockchain
According to the leaked messages, determination mightiness person been astir 30 antecedently unreported victims of Conti, including Xerox (XRX), the iconic photocopier maker, Crystal said. Xerox was known to person been hacked by a ransomware pack successful 2020; however, cybersecurity experts linked the hack to the Maze gang.
It’s not wide from the chat logs whether Xerox paid the ransom. In 2020, lawsuit support-related information from Xerox was leaked, suggesting the institution refused to wage the ransom and saw its interior information leaked arsenic a punishment, ZDNet reported. Xerox declined to remark for this story.
Some different attacks astatine the aforesaid clip were decidedly successful.
In particular, Conti members sermon attacks connected Canadian excavation shaper Softub and respective U.S.-based companies: proscription institution Piper Logistics, concatenation retailer Sam’s Furniture, outdoor instrumentality shaper Clarus and currency handler Loomis.
Softub Director of Operations Tom Lalonde told CoinDesk successful an email the institution had its information saved successful cloud-based backups truthful it didn’t wage the ransom.
However, the onslaught “did make a full clump of problems,” Lalonde said. The institution “had a fewer ransomware attacks during that timeframe,” helium added.
Piper Logistics, Sam’s Furniture, Clarus and Loomis did not respond to requests for comment.
In the messages, the Conti members notation attacking 89 companies, astir of them based successful the U.S., on with a clump of Canadian, Australian and European corporations. It’s not wide however galore of the attacks were palmy and led to bitcoin payouts but the standard of operations decidedly seems massive, Crystal said successful a blog post published connected Tuesday.
Conti members adjacent notation plans to infect Pfizer (PFE), the large pharmaceuticals shaper and the co-creator of a COVID-19 vaccine, but it’s not wide whether an onslaught was conducted and, if so, whether it succeeded.
Crystal besides said it located respective antecedently unreported wallets the Conti radical used, acknowledgment to those wallets being mentioned successful the chat logs: a wallet that received 200 BTC from an unidentified unfortunate connected Oct. 26, 2020; a wallet that collected payouts from assorted attacks; a wallet pack members utilized to negociate operational expenses; and others.
According to the leaked chat logs, Conti had immoderate big plans related to crypto and blockchain. For example, the members person been entertaining the thought of creating their ain peer-to-peer cryptocurrency marketplace and a smart-contract-based tool for extortion.
The radical besides discussed disinformation campaigns to dump the prices for smaller cryptocurrencies and mightiness person been progressive successful the Squid Game-themed exit scam, information researcher Brian Krebs wrote.
But the group’s interactions with crypto, for the astir part, person been much mundane and exemplify however precisely crypto works and however it is converted into fiat wealth successful the transgression underworld.
The leaked messages amusement the group’s mundane operations: Members sermon improvement of the malicious code, what works and what doesn’t, what payments are owed for IT services the radical uses and enactment with different transgression groups.
According to the messages reviewed by CoinDesk, Conti members utilized crypto, among different things, to wage for unreality servers and bundle licenses. For example, successful 1 message, a subordinate nicknamed Defender is asking Stern to nonstop him $700 successful bitcoin to wage for the server the radical is using.
Although crypto serves arsenic the main outgo method betwixt the radical members, astir preferred to person their paychecks successful fiat. For that, Conti members utilized an over-the-counter (OTC) broker, which is simply a fashionable method successful Russia and Ukraine, wherever planetary centralized exchanges historically person been scarce.
In a connection to a caller subordinate successful July 2020, Stern explains however to person a monthly paycheck: The caller enlistee should find an OTC table with a favorable terms connected the Russian-language OTC aggregator Bestchange.com, make an bid to merchantability bitcoin for a debit paper transportation and supply Stern with a deposit code the OTC would generate.
This way, the “employee” would person wealth successful fiat straight to his debit card, portion the brag would walk crypto, fundamentally utilizing the OTC arsenic a outgo processor.
OTCs are besides the main transmission of the ransom cashouts, chat logs show. In 1 dialogue, a subordinate named Revers explains however the extorted crypto is sold via OTC brokers: When transferring bitcoin, Conti sends wealth mules, oregon the alleged drops, to cod the cash, truthful that the existent owners of the ill-gotten bitcoin stay incognito.
“For $300K, cipher would spell to Russia to look for you,” Revers adds.
Payment for IT products and server usage often requires fiat liquidity, too, and that’s wherever the crypto-native cyber criminals whitethorn look immoderate obstacles paying their bills. In a chat betwixt 2 members, Strix and Carter, Strix asks however Carter pays for servers via PayPal (PYPL), arsenic OTC brokers lone woody with the larger sums than the 7 euros per period Strix needed to wage for utilizing his idiosyncratic server.
Carter explains that first, helium sells crypto connected the peer-to-peer marketplace LocalBitcoins for a slope transportation to his debit card, and the paper is linked to a PayPal account. The card, helium adds, is “phantom,” meaning, it doesn’t beryllium to him – supposedly, a wealth mule is used.
The PayPal relationship is verified, Carter says, raising the question if the PayPal relationship he’s utilizing besides belongs to a wealth mule, oregon has been verified utilizing stolen oregon forged ID documents – a transgression work disposable and flourishing successful the darknet, arsenic a CoinDesk investigation earlier showed.
Other than the no-name OTC, Conti besides utilized immoderate known services to currency retired ransom money, Crystal said. Conti-associated addresses sent bitcoin to: the present sanctioned Russian OTC Suex; the Hydra darknet marketplace; the RenBTC exchange; and addresses associated with Wasabi, a non-custodial wallet that lets users obfuscate the origins of their funds by merging them with different people’s bitcoin successful alleged CoinJoin transactions.

 3 years ago
3 years ago







 English (US)
English (US)