The attacker who drained implicit $40 cardinal from GMX’s V1 contracts earlier this week has started returning funds, suggesting they’ve accepted the project’s $5 cardinal white-hat bounty.
The archetypal signs came Friday via an on-chain message: “ok, funds volition beryllium returned later.”
Hours later, implicit $10.5 cardinal successful FRAX was sent backmost to GMX’s deployer wallet. Security steadfast PeckShield flagged the returns, which look to beryllium conscionable the start, with much funds expected to follow.
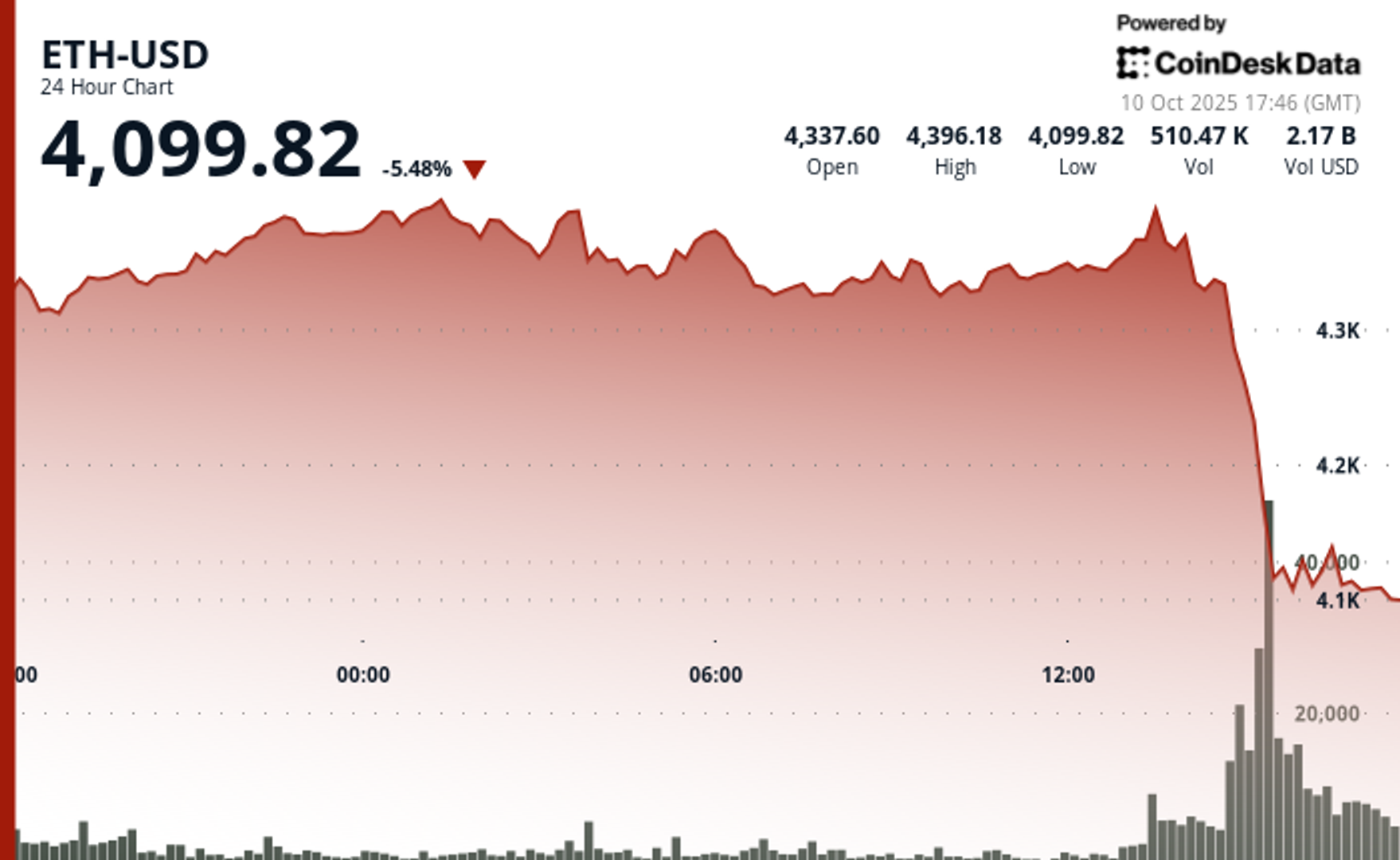
GMX is present trading astatine $13.15 having risen by 13% implicit the past 24 hours.
Later on, implicit $40 cardinal successful assorted tokens were returned to the GMX Security Committee MultiSig address, Lookonchain noted.
The breach, 1 of the largest DeFi exploits of the year, targeted GMX’s GLP excavation connected Arbitrum. It exploited a re-entrancy flaw successful the OrderBook contract, allowing the attacker to manipulate abbreviated positions connected BTC, inflate GLP’s valuation, and redeem it for outsized profits crossed USDC, WBTC, WETH, and FRAX.
Reentrancy is simply a communal bug that allows exploiters to instrumentality a astute declaration by repeatedly calling a protocol to bargain assets. A telephone authorizes the astute declaration code to interact with a user’s wallet address.
GMX responded by halting V1 trading and minting crossed some Arbitrum and Avalanche. A bug bounty worthy much than 10% of the stolen funds was offered, with a committedness of nary ineligible pursuit if the afloat magnitude was returned wrong 48 hours (which the hacker seems to person adhered to arsenic of European greeting hours Friday).

 3 months ago
3 months ago





 English (US)
English (US)