DNS mightiness beryllium disregarded arsenic aged technology, but it could supply greater code functionality and easiness of verification.
This is an sentiment editorial by Mark Jeftovic, cofounder and CEO of easyDNS Technologies Inc. and writer of “Managing Mission Critical Domains and DNS.”
From the infinitesimal I discovered Bitcoin backmost successful 2013, I knew determination would yet person to beryllium a mode to notation wallet addresses utilizing human-readable labels.
The large occupation with Bitcoin’s agelong addresses is that they are not memorable, and contempt the pseudonymous oregon anonymous features of Bitcoin, a batch of the clip you privation to beryllium capable to easy asseverate oregon verify that a wallet code belongs to a circumstantial entity — deliberation donations to a foundation oregon a crowdfund. This affects each blockchain.
As a DNS (domain sanction system) guy, I’ve seen this movie before: DNS was invented to lick the aforesaid occupation with IPv4 addressing. Over clip DNS evolved to bash overmuch much — not lone did DNS adhd the capableness to resoluteness IPv6 addresses, but it is besides progressively utilized to convey metadata astir a namespace. Think SRV records, NAPTR’s, RBL blocklists, response argumentation zones (RPZs) and the ubiquitous TXT record (which is utilized for SPF, DMARC, DKIM and thing other that doesn’t natively acceptable the protocol).
Along comes Bitcoin and we person the aforesaid problem, writ large.
The Problem Specific To Bitcoin And Lightning
It’s looking similar overmuch of the outgo transaction enactment volition determination to Layer 2 with protocols similar Lightning, and astir precocious the advent of the Lightning Address.
Lightning Addresses rely connected the LNURL-pay protocol, and they look beauteous overmuch similar an email address:
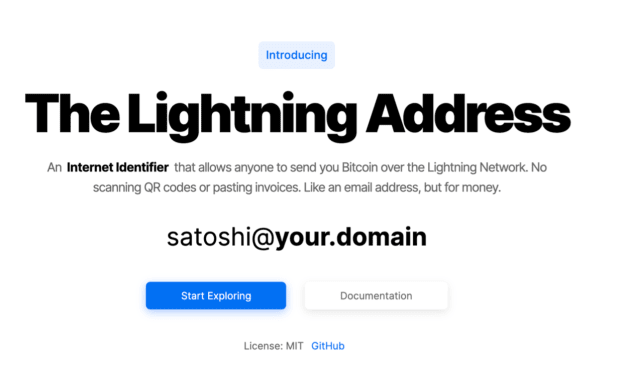 via: https://github.com/andrerfneves/lightning-address/blob/master/README.md
via: https://github.com/andrerfneves/lightning-address/blob/master/README.mdThe email code nomenclature is the cleanable mode to convey individuality information. It easy demarcates organizations and further subdivides to units oregon radical wrong it. Everybody is already utilized to this format and arsenic we’ll see, has the imaginable to convey overmuch much accusation than destination mailboxes.
For years I was anticipating this format becoming the de facto modular for individuality endpoints with Session Initiation Protocol (SIP) and XMPP.
SIP and XMPP didn’t instrumentality implicit the satellite rather the mode I expected them to (at slightest not yet) and for a while, identifiers started gravitating toward centralized platforms similar Twitter handles and Github idiosyncratic IDs. I ever recovered this quizzical, particularly among Bitcoiners.
With Lightning Addresses we spot a way backmost toward decentralized identifiers, since email addresses are themselves decentralized, wrong the limits of the DNS strategy itself (more connected that below).
There’s lone 1 problem: the LNURL spec arsenic defined is missing a level of abstraction. Without it, the usage lawsuit for Lighting Addresses becomes precise constrained.
Given the Lightning Address:
That means nether the existent specification, the outgo descriptor volition beryllium located at:
https://example.com/.well-known/lnurlp/satoshi/
But what if Satoshi doesn’t person entree to the example.com webserver? If we instrumentality with the email code analogy: conscionable due to the fact that you person this arsenic your code doesn’t mean the server with the matching hostname is wherever the email gets delivered.
In information that’s astir apt not the lawsuit much often than it is. For this crushed determination exists the MX grounds benignant successful DNS, which adds an other level of indirection to power the destination for email. They whitethorn nonstop email transportation to hostnames operating nether a wholly antithetic domain sanction (think astir radical who usage an outer email provider, but with their ain customized domain).
The aforesaid happening needs to hap with Lightning Addresses for mostly the aforesaid reasons. The hostname to the close of the ‘@’ whitethorn not person a webserver astatine all, oregon the idiosyncratic is unduly confined to utilizing a Lightning Address wherever the hostname constituent tin lone beryllium that of the webserver wherever the JSON record is hosted. That tin beryllium a occupation erstwhile publishing a Lightning Address that the idiosyncratic wants to alteration down the road.
As a DNS guy, the solution seemed evident but I was blameworthy of overthinking it:
In 2017 I was invited by what was past the Ethereum Name Service Working Group to a gathering successful London to enactment retired the specification for the ENS registry.
I near that gathering reasoning that determination needs to beryllium a caller DNS assets record, a caller grounds benignant that would beryllium capable to notation blockchain resources from wrong the bequest DNS.
In my caput it would look thing similar a SRV oregon NAPTR record, which had antithetic fields for protocols, ports and weightings (the information that web browsers contiguous inactive don’t look astatine SRV records for web addresses is 1 of the large missed opportunities of the net age).
My moving shorthand for it was “BCPTR” for “Blockchain Pointer” and it had an overcomplicated, convoluted specification for pointing retired precisely which blockchain a grounds was pointing astatine and what benignant of assets it was.
Then successful the Lightning GitHub issue, wherever the LNURL RFC was being discussed, somebody suggested simply prepending an code with the “_lud16” subdomain.
Using underscores to differentiate definite naming attributes from existent hostnames has been astir for awhile. It was utilized successful the archetypal SRV RR spec RFC2872 and aboriginal described arsenic “underscore scoping” in RFC 8552.
The proposition instantly exploded successful my encephalon and I realized that I had been overthinking this for years.
A scoped statement successful DNS, similar _tcp oregon _udp, are lawsuit insensitive and we spot them successful SRV and NAPTR records for usage successful SIP, VOIP and ENUM applications, load balancing, not to notation successful TXT records for DKIM and DomainKeys.
Pretty good immoderate valid DNS label, similar _lud16 oregon _btc, provides america with a mechanics to confine a effect to a query matching the scope, nether the genitor node successful the DNS tree.
Meaning:
$ORIGIN example.com.
_ie.test IN TXT “this is simply a test”
_eg.test IN TXT “this is simply a abstracted test”
A DNS query for benignant TXT connected “test.example.com” volition not instrumentality an reply (NXDOMAIN).
A DNS query for benignant TXT connected “_ie.test.example.com” volition only return a effect for the archetypal record.
A DNS query for benignant TXT connected “test._ie.example.com” volition only return the 2nd record.
In different words, we person aggregate TXT records for the test.example.com leaf, however, we volition lone instrumentality the 1 queried with the scoped label, the 1 that begins with an underscore.
It turns retired this is rather almighty for our purposes. It is besides the easiest, optimal solution successful our usage lawsuit because:
- Everybody tin usage it.
- It’s a format radical easy recognize.
- It tin beryllium retrofitted onto immoderate existing email code via DNS.
- It provides the quality for a json grounds to beryllium someplace different than the server (like however an MX grounds functions).
- Can supply immoderate benignant of payload.
- Can enactment crossed each blockchains.
How Underscore Scoping Could Be Used In Blockchains
By taking the email code format utilized successful Lightning Addresses: , we tin usage the normal via the DNS to specify each kinds of endpoints for the aforesaid identity:
$ORIGIN bombthrower.com.
_lud16.markjr IN TXT "https://my.ln-node/.well-known/lnurlp/markjr"
_btc.markjr IN TXT "bc1qu059yx6ygg9e6tgedktlsndm56jrckyf3waszl"
_ens.markjr IN TXT "0xEbE7CcC5A0D656AD3A153AFA3d543160B2E9EdFb"
We tin get determination from present without breaking thing already successful place:
- Applications already utilizing LNURL code tin ever support utilizing that
- Applications tin adhd the DNS lookup
But DNS Is Centralized!
It’s existent that DNS has an inverted histrion operation that terminates astatine the basal “.”. But adjacent that basal is reasonably decentralized, comprising thousands of servers operated by astatine slightest 13 disparate operators. The bequest DNS whitethorn beryllium logically centralized but successful world functions much similar a decentralized federation of sorts.
Even this is changing, evolving. I deliberation wherever we yet extremity up is wherever namespaces straddle some the existing inverted histrion basal and afloat decentralized blockchains.
Some of this is already present today: you could usage thing similar Stacks and .btc domains which pins to Bitcoin and determination volition astir apt beryllium different namespaces built straight atop Bitcoin.
Not each decentralized namespaces person bequest DNS resolvers, but that volition alteration too. There is besides enactment being done connected a new DNSresolvers implementation which volition resoluteness Stacks, .btc, and HNS domains by Handshake, and Unstoppable top-level domains. You tin trial it via lookups to alpha.dnsresolvers.com:
% excavation +short easydns.btc @alpha.dnsresolvers.com
3.14.49.122
(This server is proof-of-concept and volition spell distant successful the future, please don’t adhd it to your resolv.conf.)
All This, And It Solves The Fake Twitter Handle Problem Too!
Once we marque it a normal to usage underscore scoping, we find we tin lick each mode of problems utilizing existing methods.
Let’s look astatine the fake Twitter grip occupation that plagues the Bitcoin space.
The information operation of a Twitter idiosyncratic looks similar this:
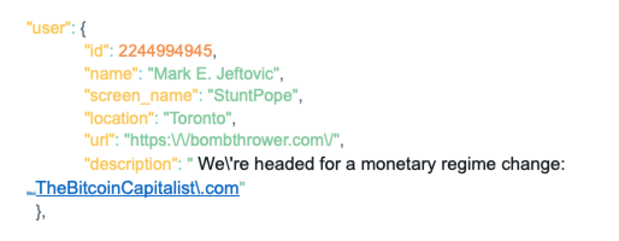
With underscore scoping we tin asseverate the existent Twitter grip from the hostname successful the url constituent utilizing the pursuing convention:
$ORIGIN bombthrower.com.
stuntpope._twitter IN TXT “StuntPope”
*._twitter IN TXT “fake”
On its own, this doesn’t bash anything. Nobody is going to unfastened up a terminal model and type:
“dig -t TXT +short stuntpope._twitter.bombthrower.com”
… to find retired if the idiosyncratic DMing you, “How is your trading going today?” is truly me, oregon 1 of the legions of StuntPope imposters retired determination connected Twitter. (I’m kidding of course, cipher successful their close caput would impersonate me. But for a batch of the fintwit luminaries, this is simply a existent problem.)
But what tin hap if this becomes the convention, is developers tin physique speedy and soiled hooks into their apps to bash these lookups.
When a fake Twitter illustration impersonates someone, they typically transcript each the information verbatim, including the hostname successful the URL tract of the Twitter profile. If the existent idiosyncratic has the records outlined above, past the normal of looking up the fake Twitter grip astatine the real URL volition miss the existent _twitter TXT grounds for the existent profile, and deed the wildcard record, causing a mismatch.
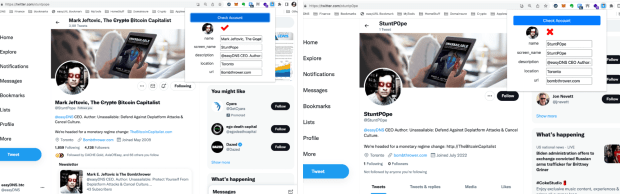
We’ve released a proof-of-concept Chrome hold done the easyDNS Github, which does conscionable that with 3 modes:
A) No accusation asserted;
B) The illustration matches the accusation asserted;
C) The illustration does not lucifer the accusation asserted (it’s a fake).
All this and more, tin beryllium done utilizing precise elemental conventions successful a ubiquitous protocol that’s already deployed.
Conclusion
Wallet addresses lend themselves to needing immoderate benignant of naming mechanism. There are aggregate usage cases wherever the request to securely asseverate an code from an individuality takes precedence implicit pseudonymity oregon anonymity.
Further, to usage human-readable labels oregon identifiers, we request an abstraction furniture that provides flexibility and a format that is easy recognizable.
Finally, we tin execute each this utilizing the DNS, which already underpins the method infrastructure of the internet, is already a decentralized federation and connected its mode to anchoring connected decentralized Layer 1 protocols. We tin bash truthful without adding immoderate caller grounds types oregon making immoderate protocol additions to the existing specifications.
This is simply a impermanent station by Mark Jeftovic. Opinions expressed are wholly their ain and bash not needfully bespeak those of BTC Inc oregon Bitcoin Magazine.

 3 years ago
3 years ago








 English (US)
English (US)